1. Click
Rule >
+ New to enter the
New Rule interface, as follow:
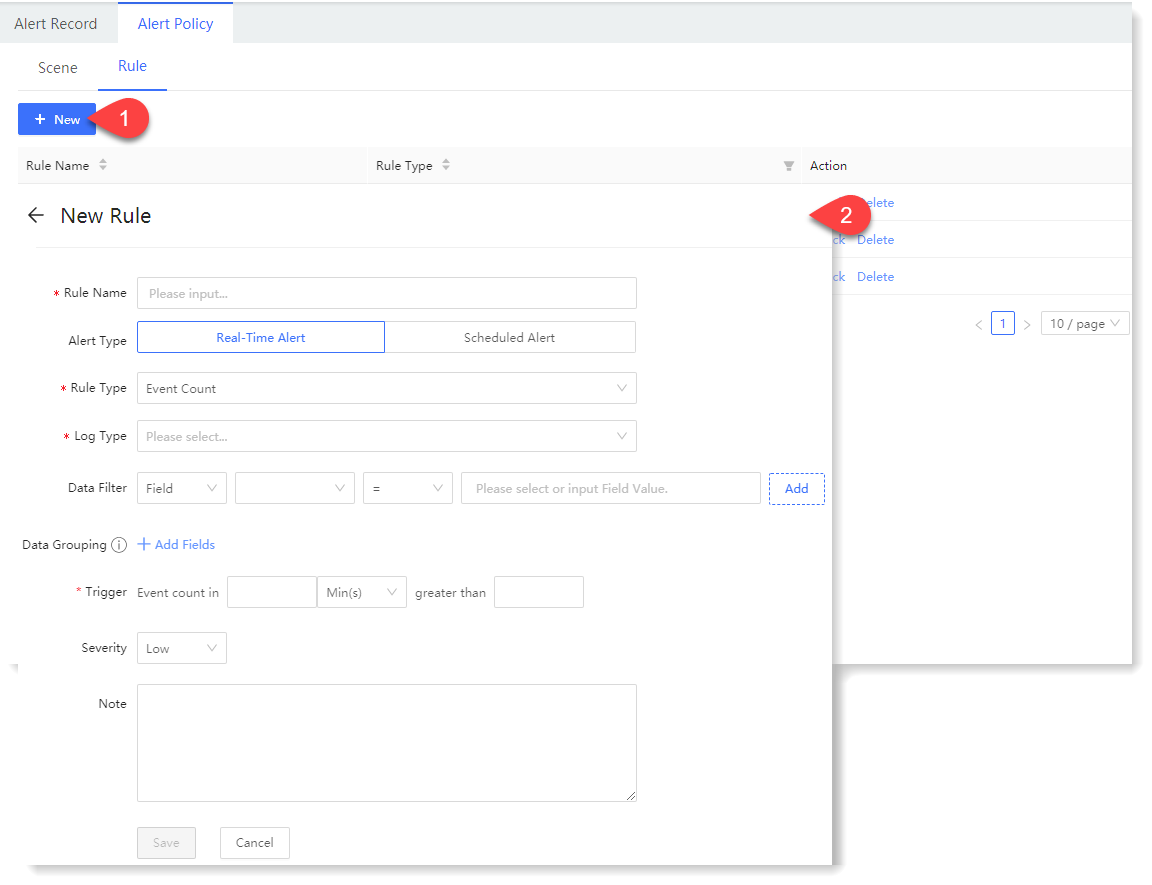
• Alert Type: Real-Time Alert
| Field Name |
Description |
| * Rule Type |
It includes 2 types: Event Count and Field Aggregation |
| * Log Type |
The configuration of saved log type as alert data source |
| Data Filter |
The data source can be filtered by Field or Keyword:
Note: You can add multiple data filter conditions and connect them by the logical operators AND/OR. |
| Data Grouping |
It is equivalent to GroupBy in SQL, grouping alert data according to the specified fields, and up to 5 grouping fields can be added:
• If no group fields are added, the aggregation is for all alert data;
• If data grouping is enabled, when an alert policy is triggered to generate an alert record, the group field can be viewed in the optional Field Gear display list on the alert record page.
Note: The alias is the name of the field displayed on the alert record page, which shows by default the original field name, and the alias cannot be repeated. |
| * Trigger |
• Event Count as Rule Type: The number of alert occurrences of a certain type of event that exceeds the threshold range in a given time period triggers the alert.
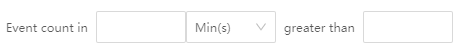
• Field Aggregation as Rule Type: A certain aggregation value of a field exceeds the threshold range in a given time period triggers the alert. 
Note: If the selected field is a non-numeric type, the aggregation type can only be selected with Unique Count. If the selected field is a numeric type, the aggregation type can be selected with Unique Count, Min, Max, Avg, Sum, and the default is Unique Count. |
| Severity |
The urgency of alert, including Low, Medium and High risk. |
• Alert Type: Scheduled Alert
| Field Name |
Description |
| * Rule Type |
It supports source log non-aggregation alert. |
| * Monitoring for |
The host object to be monitored, including Host and Host Group:
• Host as Object: You can select multiple hosts for alert monitoring;
• Host Group as Object: You can select all hosts in host group for alert monitoring.
Note: The monitoring object of the source log non-aggregation alert is the host with the configuration of AR-Agent aggregation task. For details, please refer to the section Agent Management . |
| * Trigger |
An alert will be triggered if the monitored host has not aggregated a log file for longer than the set threshold, which is 24 hours by default.
 |
| Severity |
The urgency of alert, including Low, Medium and High risk. |
2. After configuration, click
Save to finish rule creation.






















